This article is sponsored by VLCM.
Cyberattacks are not only more frequent, but they’re also more destructive. From ransomware incidents that paralyze global logistics operations to phishing schemes that compromise sensitive financial data, the effects of a cybersecurity breach can ripple through every facet of an organization.
Despite mounting evidence and high-profile headlines, many organizations still treat cybersecurity as a technical concern rather than a core business risk. One of the most effective ways to bridge this gap is conducting a risk assessment, a structured, strategic evaluation of an organization’s vulnerabilities, the threats it faces, and the potential impact of those threats.
Although this article emphasizes cyber risks — organizational risk extends well beyond threats such as ransomware. A comprehensive cybersecurity risk strategy should also account for natural disasters, insider threats, system failures, pandemics, and other disruptions that can significantly impact operations.
What is a Cybersecurity Risk Assessment?
A Cybersecurity Risk Assessment is a systematic process used to identify, analyze, and evaluate threats and vulnerabilities that could adversely impact an organization’s operations, assets, or personnel. It considers both the likelihood of adverse events and the severity of their potential impact. The objective is to equip decision-makers with actionable insights to prioritize risks and implement effective safeguards.
Organizations often rely on established frameworks to guide this process. NIST SP 800-30 offers a structured methodology for assessing threats and vulnerabilities, while ISO/IEC 27005 supports ISO 27001 information security programs.
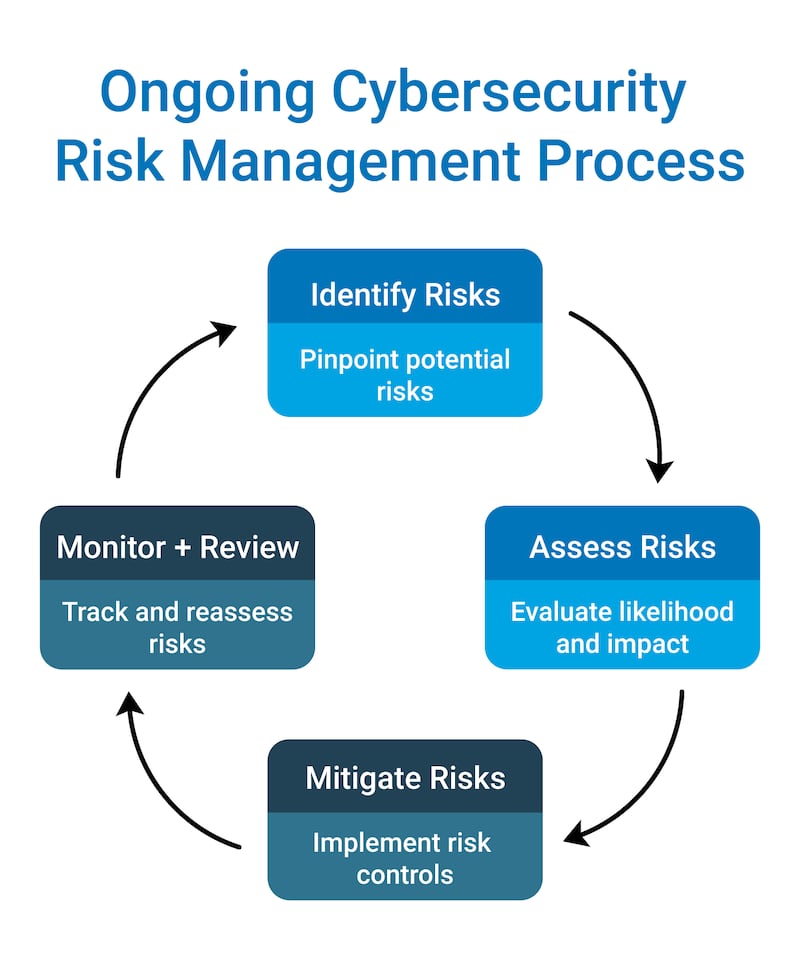
The core components of a Cybersecurity Risk Assessment program:
- Asset Identification: Define what needs protection (e.g., data, systems, infrastructure, people, reputation).
- Threat Identification: Determine potential sources of harm (e.g., cyberattacks, natural disasters, insider threats, system failures).
- Vulnerability Identification: Identify weaknesses that could be exploited by threats (e.g., unpatched systems, poor access controls, lack of training).
- Risk Analysis: Assess how threats exploiting vulnerabilities would impact assets.
- Risk Evaluation (Prioritization): Compare and rank risks against organizational risk appetite/tolerance.
- Risk Treatment (Mitigation Options): Define strategies: accept, avoid, transfer (insurance/outsourcing), or mitigate (controls, policies, technology).
- Documentation & Reporting: Record findings in a risk register.
- Continuous Monitoring & Review: Regularly track risks and controls to confirm they remain effective, adjusting as new threats, vulnerabilities, and business priorities emerge.
It’s important to note that risk assessments are not one-time exercises; they work best as an ongoing practice that strengthens resilience, guides resource allocation, and keeps pace with evolving regulatory requirements. By building continuous monitoring and review into the process, organizations can adapt to new threats and shifting business objectives while maintaining a proactive security posture.
In this way, a Cyber Risk Assessment becomes more than a compliance checkbox. It serves as a foundation for strategic and financial protection, giving leaders the visibility they need to anticipate risks and act before issues escalate.
The financial fallout of unidentified risks
The impact and cost of a cyberattack can be extensive and reach deep into an organization’s operations. Key areas of concern include business disruption, reputational and brand damage, remediation expenses, regulatory compliance violations and associated fines, legal liability, as well as the compromise of data and intellectual property. Below, we take a closer look at each of these critical areas.
Business disruption
Operational downtime is often the most immediate and measurable consequence of a cyberattack. Whether it’s a retailer unable to process transactions, a hospital locked out of patient records, or a logistics firm frozen in place, downtime equals lost revenue.
For instance, a ransomware attack can halt operations for days or even weeks, leading to missed sales, broken supply chains, and shaken customer confidence. Once the breach becomes public, customers may walk away, vendors may withdraw, and new business can stall.
According to IBM’s Cost of a Data Breach Report, the average cost of lost business alone exceeds $1.5 million.
By highlighting mission-critical systems and estimating the financial impact of downtime, a risk assessment helps leaders prioritize protection strategies and reduce disruption.
Brand and reputational damage
Trust is the currency of modern business. A single breach involving personal or confidential information can shatter customer confidence and damage an organization’s reputation, often irreparably.
Reputational damage can lead to lost clients, diminished investor confidence, negative media coverage, and long-term brand erosion. In regulated industries, the stakes are even higher.
By pinpointing the data most damaging to lose, a risk assessment informs crisis planning and enables faster, more transparent response strategies.
Cost of remediation
Incident response efforts are complex and costly. Beyond technical remediation, organizations often incur costs for forensic investigations, legal counsel, crisis communications, customer notifications, identity protection services, system rebuilds, among other requirements. These expenses can quickly escalate, especially when root causes are unclear, or lawsuits are pending.
Remediation also diverts critical resources away from normal operations, disrupting business continuity and delaying strategic initiatives. IT and security teams may be forced to pause planned projects or redirect budgets to address urgent recovery efforts.
See Related: Don’t wait for a crisis to strike – download your free Incident Response Plan Template now!
Anticipating potential costs, modeling financial exposure, and planning recovery efforts up front helps organizations respond more effectively when incidents occur.
Compliance violations
For organizations subject to regulatory frameworks such as HIPAA, PCI-DSS, GDPR, or CMMC, a breach can trigger mandatory reporting, regulatory audits, and substantial penalties. For instance, under GDPR, violations can result in fines of up to 4% of annual global revenue.
Aligning security controls with regulatory requirements and surfacing gaps early helps prevent violations, while thorough documentation provides a record of due diligence — an essential defense during investigations and audits.
Legal liability
In the wake of a breach, legal consequences are becoming increasingly common. Organizations face lawsuits from customers, business partners, and shareholders alleging negligence, breach of contract, or failure to protect sensitive data. Litigation often extends beyond direct financial damages and can include discovery requests, expert witness testimony, and ongoing legal fees that last for years. Shareholder actions may also target executives and board members personally, citing failures in oversight or governance. Even if technical recovery is swift and systems are restored, the long-term legal and financial repercussions, including regulatory investigations, reputational damage, and erosion of customer trust, can be crippling to the business.
Cybersecurity risk assessment services provide foresight into these potential liabilities and help organizations proactively structure risk transference strategies such as cyber insurance coverage, contractual liability shifts with vendors, and governance enhancements that reduce exposure and strengthen resilience.
Beyond IT: The strategic role of Cybersecurity Risk Assessments
Cybersecurity risk assessments are essential to long-term operational success, forming the foundation of disaster recovery and business continuity planning to ensure critical functions remain operational during crises. They also demonstrate a visible commitment to security that clients, partners, and investors increasingly expect. This diligence builds trust, strengthens reputation, and often serves as a competitive advantage in procurement and partnership decisions.
Beyond these operational advantages, Cybersecurity Risk Assessments are no longer just about checking compliance boxes or avoiding the next breach. They have become a boardroom conversation — a way for leadership to understand where the business is vulnerable, where investments have the greatest impact, and how risk aligns with strategy. By treating assessments as a continuous discipline, organizations demonstrate to employees, customers, and investors that resilience is part of their culture. In the end, a Cybersecurity Risk Assessment isn’t only about protecting systems; it’s about protecting confidence, enabling smarter decisions, and ensuring the business is positioned to grow in an uncertain environment.
VLCM is here to help you be more cyber secure
A Cybersecurity Risk Assessment is the first step in identifying threats to your organization. Partner with VLCM to uncover risks, strengthen continuity, and protect your organization’s future. Here’s how to get started.

